08 January 2025
Eito Tamura
tl;dr
When organisations implement modern IDS monitoring solutions, stealthy evasion during network or host enumeration may not always be feasible. In such cases, attackers might employ SYN port scanning with spoofed source IP addresses to intentionally generate alerts, diverting the SOC team's attention through deceptive tactics. SOC teams should be aware of these techniques to quickly identify the true origin of the attack and maintain effective incident response.
Offensive Deception
Modern detection systems are continuously evolving, making it increasingly challenging for attackers to evade them while remaining stealthy. When complete stealth isn't an option, attackers can still employ an alternative strategy: deception. By using deception techniques against defenders, attackers aim to mislead, confuse, or delay detection and response efforts. This approach, known as offensive deception, involves tactics specifically designed to manipulate defenders' perceptions of an attack or create false trails to obscure the real threat.
Several different techniques exist.
False Flags
Attackers intentionally plant evidence to misattribute their actions to another entity or group. This could include using tools, tactics, or IP addresses associated with known threat actors.
Noise Generation
Flooding logs or systems with benign alerts to overwhelm defenders and hide the actual attack amidst the noise.
Triggering low-severity detections, like harmless port scans, to distract security teams from more sophisticated activities happening elsewhere.
Decoy Attacks
Launching visible but low-impact attacks to divert defenders' attention while the real attack occurs in a different part of the environment.
Misinformation and Misdirection
Leaving behind fake data, such as manipulated logs or credentials, to mislead investigators about the attackers' goals or entry points.
Using deceptive naming conventions (e.g., naming malicious files to appear as legitimate system files).
Honey-Traps for Defenders
Planting resources designed to lure defenders into wasting time on irrelevant or fake artefacts.
Setting up fake indicators of compromise (IOCs) to lead security teams down false investigative paths.
In this blog, we will cover Noise Generation and Decoy Attacks using SYN port scans with spoofed source IP addresses.
Background: Network Enumeration and Host Discovery
As penetration testers or red teamers, we are often tasked with operating from an unauthenticated perspective within internal networks, simulating assumed breach scenarios. These engagements typically replicate situations where an attacker has gained limited access to the internal environment. While various techniques can be employed to launch attacks without valid credentials in an Active Directory (AD) environment, these methods are beyond the scope of this blog.
A critical step in such scenarios is network reconnaissance, which involves enumerating internal assets, hosts, and services exposed within the network to identify potential vulnerabilities. Tools such as Nmap, a widely recognised port scanning utility, play a key role in this process. Port scanning enables the identification of open ports, services, and potential vulnerabilities, laying the groundwork for further exploitation or lateral movement within the environment.
Detecting Network Enumeration
From a defender's perspective, detecting internal port scans is crucial, as they often signal potential internal compromise and require immediate investigation. In recent years, an increasing number of organisations have started implementing detection mechanisms, such as Intrusion Detection Systems (IDS) or endpoint-based solutions, to identify such activities. Modern IDS leverage a range of techniques to identify port scanning activities.
How Port Scans Are Detected
Pattern Recognition
Many IDPs solutions monitor traffic patterns and look for anomalies such as multiple connection attempts to different ports on the same host or across multiple hosts in a short time frame. These patterns are typical of port scans. For example, a large number of SYN packets sent without corresponding ACK responses (indicating half-open scans).
Threshold-Based Detection
Some systems trigger alerts when the number of connection attempts from a single source exceeds a predefined threshold within a specific time window. For example, 50 failed connection attempts in 30 seconds from the same IP.
Protocol Behaviour Analysis
Systems observe unusual behaviour in common protocols. For example, repeated connection attempts to closed ports or non-standard port ranges.
Heuristic and AI-Based Methods
Advanced solutions use machine learning to profile normal network behaviour and flag deviations indicative of reconnaissance, such as horizontal or vertical scans.
Evasion Techniques
The success of evasion techniques largely depends on the detection system in place. For example, with rule-based detection systems, a very slow port scan may go undetected. However, this approach is time-consuming and may not be viable during engagements with tight time constraints. Other evasion techniques involve leveraging legitimate services, such as web browsers or PowerShell, which are less likely to trigger signatures associated with common port scanning tools like Nmap. Additionally, Nmap provides various scanning techniques, such as SYN and FIN scans, as well as fragmented packets, to evade detection.
These methods, however, are typically ineffective against more advanced detection systems, such as those based on heuristics or artificial intelligence (AI), employed by commercial IDS like Darktrace and Vectra AI. Alternatively, host-based detection systems or Canary tokens can still trigger alerts, even from a single port scan depending on how they are configured.
Offensive Deception: SYN Spoof Scans
A SYN port scan is a reconnaissance technique attackers use to identify open ports on a target system. It leverages the TCP three-way handshake process to gather information about the target's network and services without fully establishing a connection. While this was once considered a stealthy option for port scanning, modern IDS solutions often generate alerts for such activity.
Because the SYN scan does not complete the three-way handshake, it can also be employed as an offensive deception technique using spoofed source IP addresses. By initiating SYN port scans with spoofed source IPs, attackers can generate network enumeration alerts that appear to originate from the spoofed addresses. This tactic may confuse SOC teams, diverting their attention to investigating false leads.
It is important to note that generating a large volume of SYN traffic against a host can result in a denial-of-service condition due to numerous half-open connections, a technique known as SYN flooding.
Detection Lab Setup
In our detection lab, we conducted a test using Suricata as the IDS and the Hunting ELK (HELK) to monitor and analyse alerts. The lab's setup is illustrated in the diagram below:
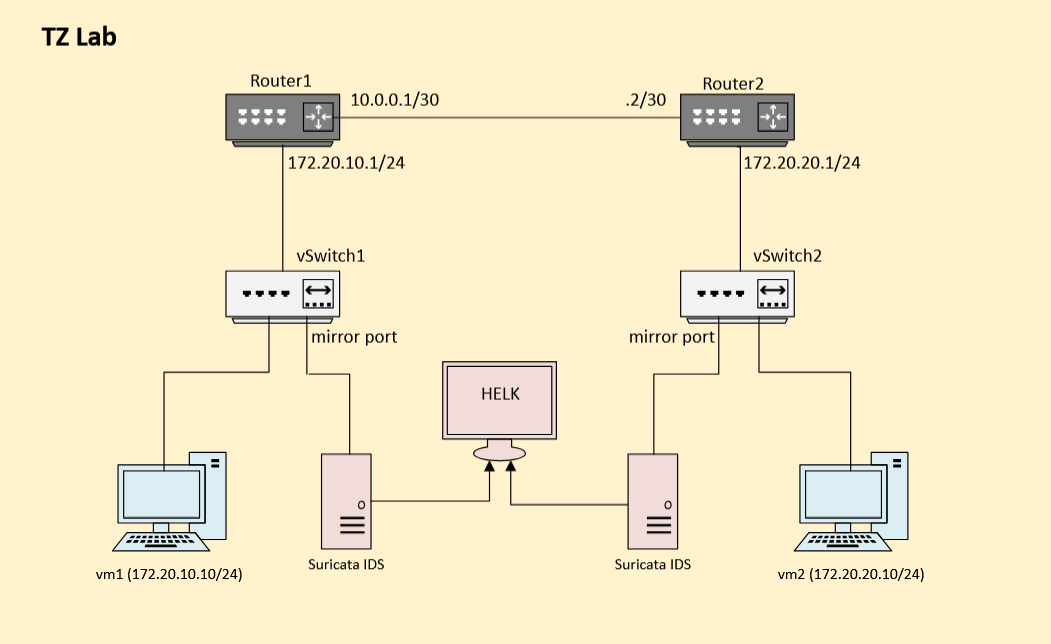
Two virtual machines, vm1 and vm2, were created in separate subnets: 172.20.10.0/24 and 172.20.20.0/24. Suricata IDS instances were connected to the mirror ports on the virtual switches to monitor real-time traffic.
Suricata
Suricata is an open-source IDS that operates by analysing network traffic in real-time and applying a set of user-defined or preconfigured detection rules to identify and respond to potential threats. I used the Nmap detection rules available here.
HELK
We've opted for the Hunting ELK (HELK) platform, utilising its capabilities for efficient log viewing and analysis at scale. It is an open-source hunting platform developed primarily for research, but due to its flexible design and core components, it can be deployed in larger environments. For detailed information on HELK, you can refer to the official documentation here.
SYN Scan with Nmap
Nmap provides the capability to perform SYN scans using the -sS option and supports the decoy scan feature (-D), which allows for generation of SYN traffic using source IP spoofing. In our lab environment, we generated traffic from vm1 and monitored the resulting alerts in Kibana.
nmap -sS -Pn -F 172.20.20.10 -D 172.30.20.10,ME,172.30.20.11 -e ens34
In Kibana, the src_ip_addr column indicates that the source IP address has been spoofed. This deceptive tactic could result in the SOC team flagging these alerts as IOCs, potentially causing confusion during their investigation.
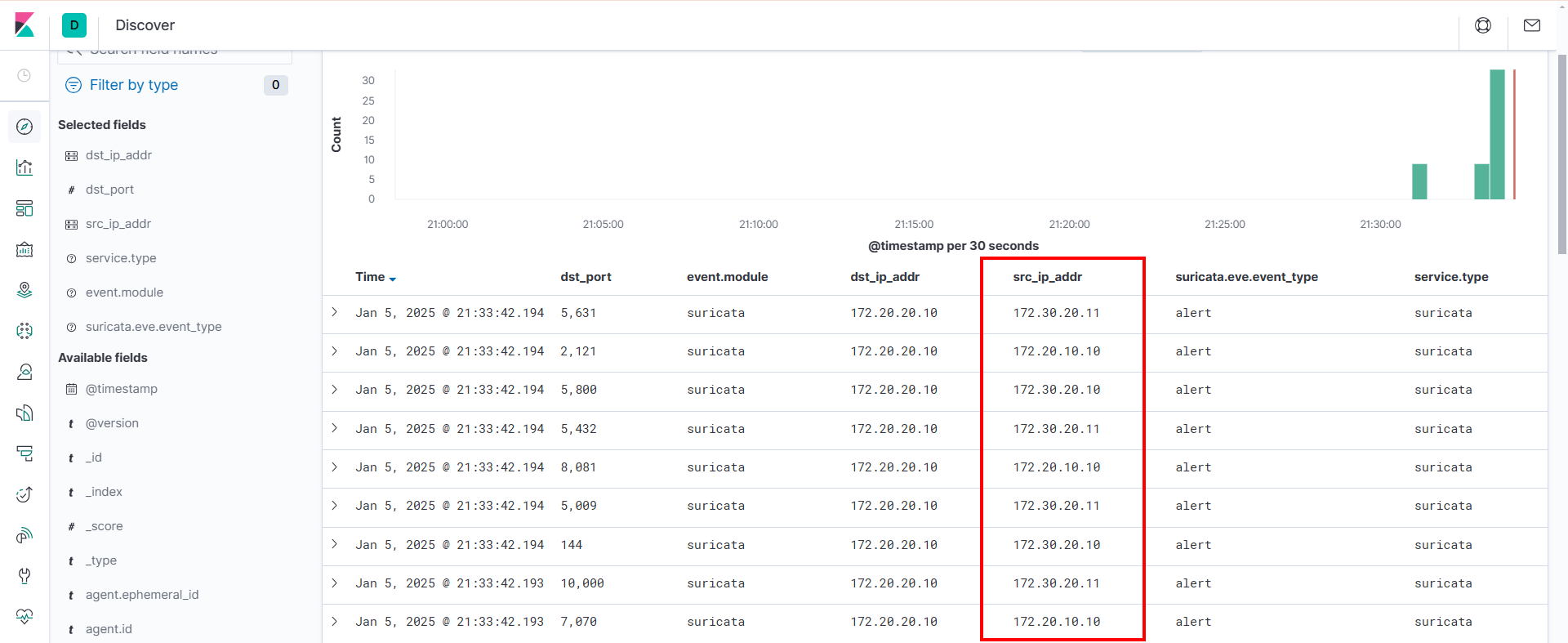
The command above performs a SYN port scan using the real IP address. To completely obscure the real IP and generate traffic exclusively with spoofed source IPs, we explored the spoof source IP option (-S) in Nmap. An example of such a command is shown below:
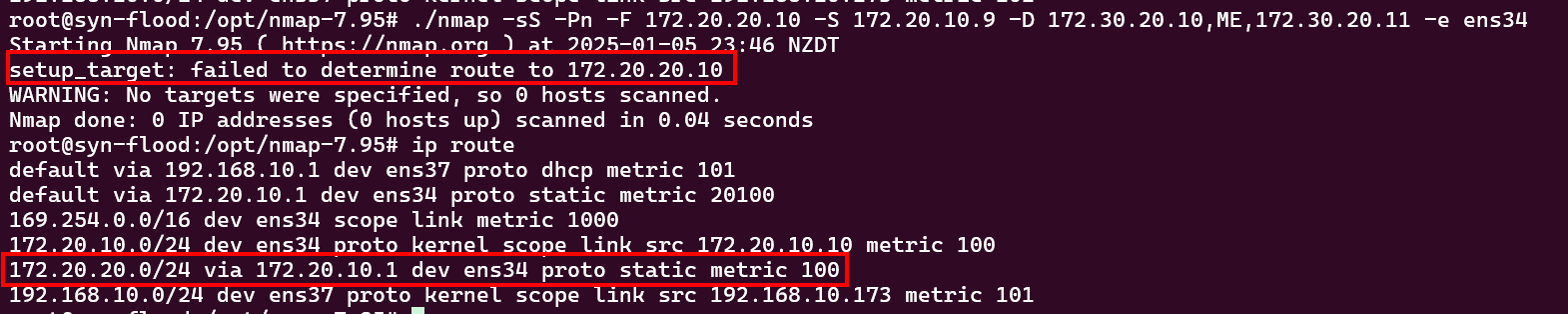
nmap -sS -Pn -F 172.20.20.10 -S 172.20.10.9 -D 172.30.20.10,ME,172.30.20.11 -e ens34
The command was intended to change the source IP address to 172.20.10.9. However, it resulted in the following error, indicating that the system could not find a route for vm2. The screenshot below also displays the existing IP routes on the host. Note: The version of Nmap used in this blog is 7.95, which was the latest at the time of writing. If anyone knows how to get around this, please let us know ;)
SYN Spoof Scanner
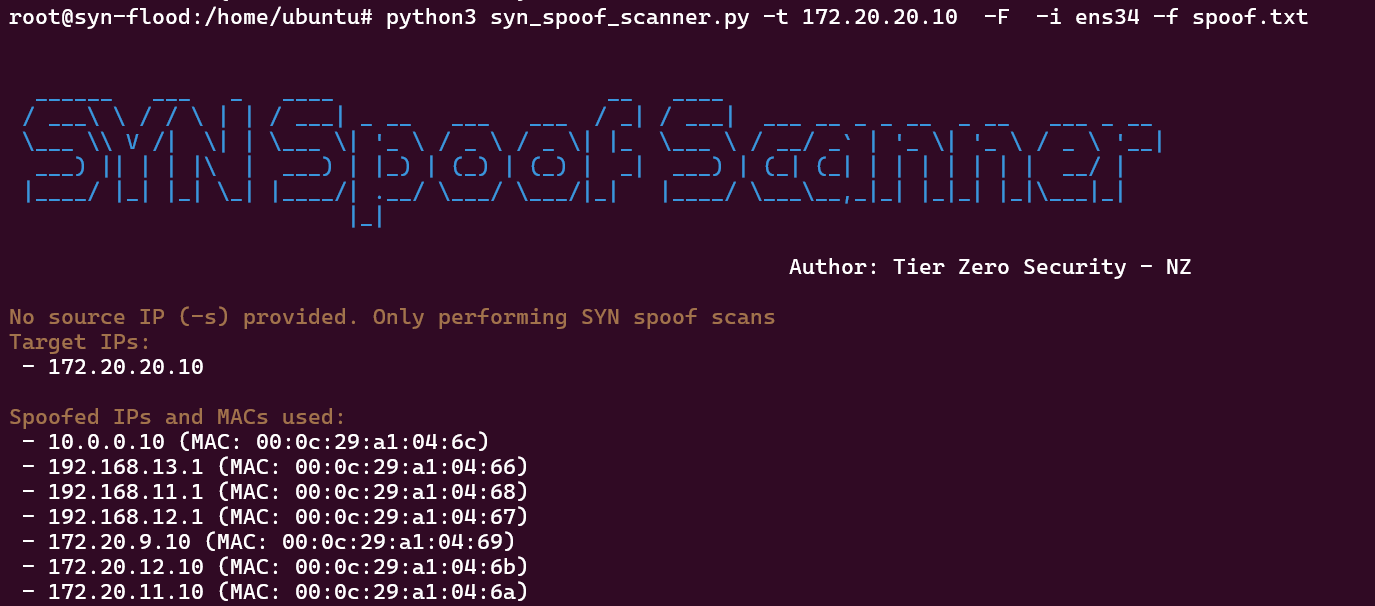
We decided to write a simple light weight tool to perform SYN scans with spoofed IP using Python Scapy. The tool is available on a Tier Zero Security GitHub repository.
The following command performs SYN port scan against 172.20.20.10 on the top 100 ports from the source IP (172.20.10.10) which is the IP address assigned to the interface (ens34), and also sends SYN packets from the IP addresses listed in the file (spoof.txt).
python3 syn_spoof_scan.py -t 172.20.20.10 -F -s 172.20.10.10 -i ens34 -f spoof.txt --open
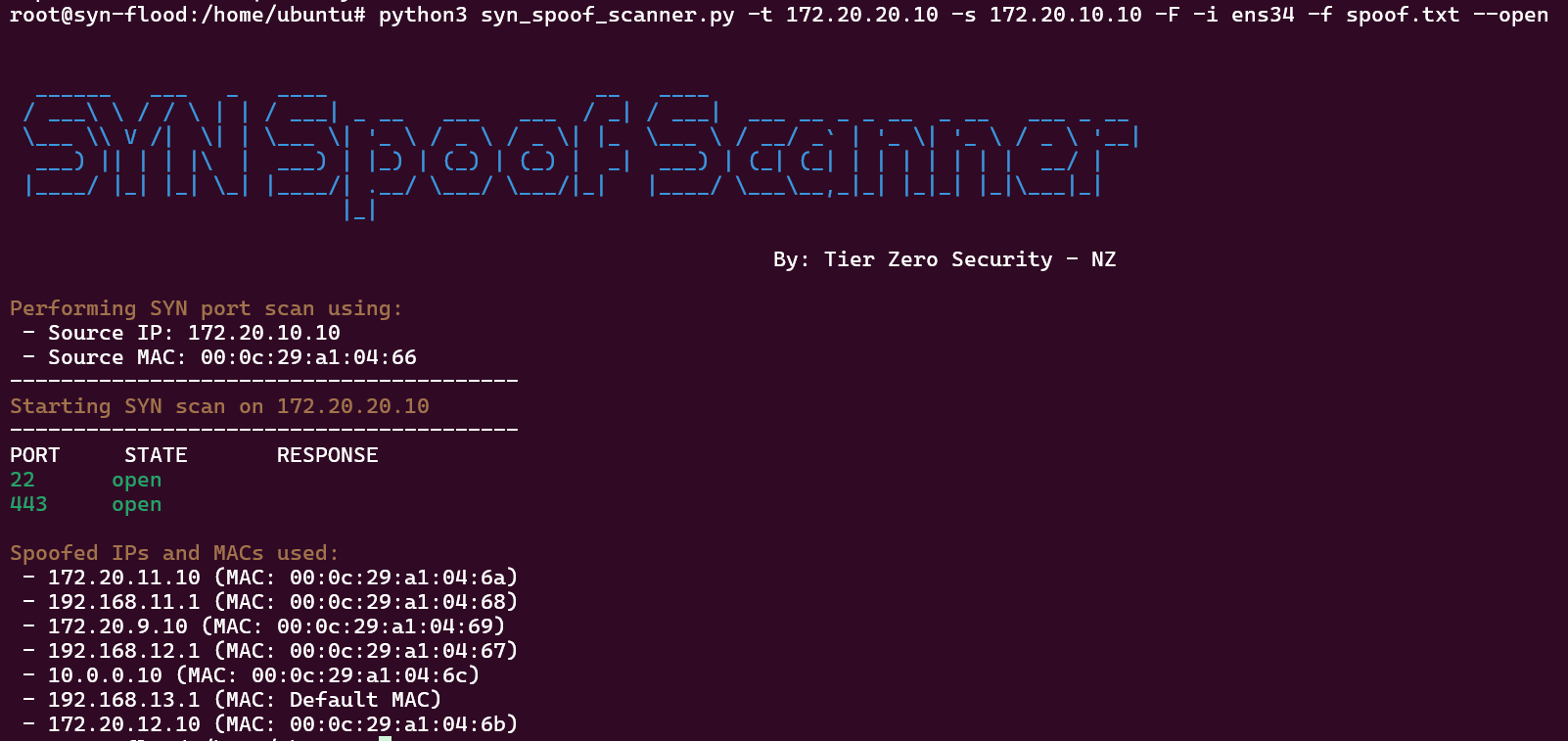
These are the alerts generated by Suricata which includes spoofed source IP addresses.
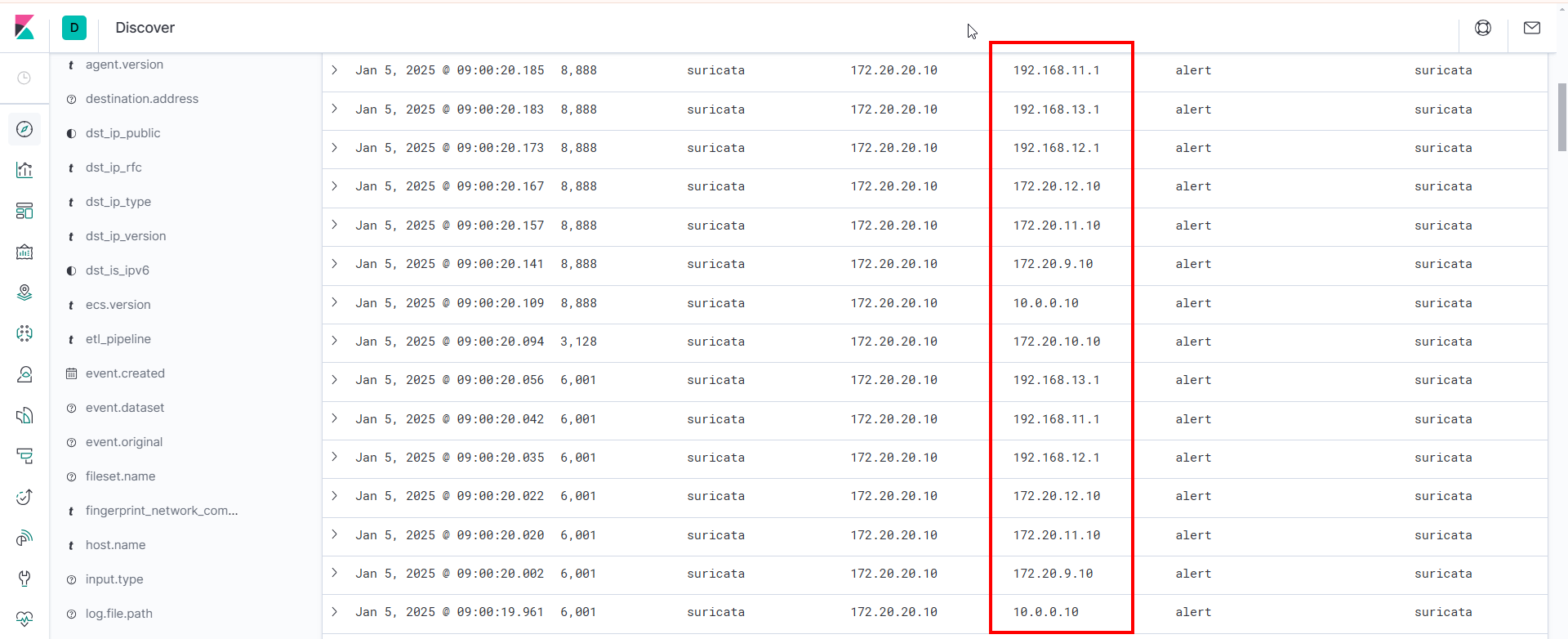
The following command does not perform SYN port scan against 172.20.20.10. Instead it generates SYN packets from the IP addresses listed in the file (spoof.txt) to the target on the top 100 ports, which can be used to alerts for deception.
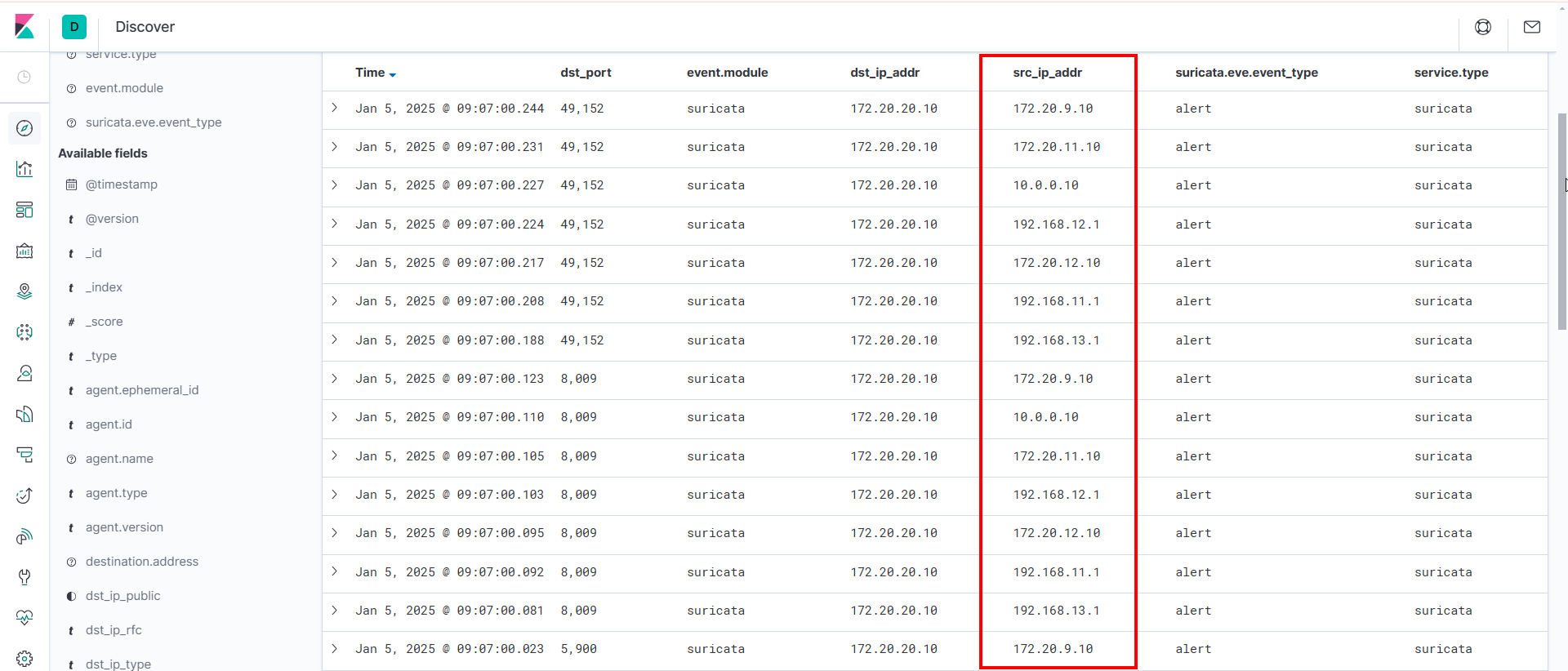
python3 syn_spoof_scan.py -t 172.20.20.10 -F -i ens34 -f spoof.txt
These are the alerts generated by Suricata only from the spoofed source IP addresses.
Summary
When stealth is not an option, offensive deception can be employed by generating SYN port scan traffic with spoofed source IPs. While this approach is not a definitive solution, it can disrupt incident response processes and provide critical additional time.
It would be worthwhile to test this in your or your clients' environments to determine whether SYN scans with spoofed source IPs generates alerts attributed to the spoofed IPs. This could also provide a valuable learning opportunity for SOC teams, particularly if they have not encountered such scenarios before, to understand offensive deception. To mitigate IP source spoofing, implementing protection mechanisms like reverse path validation (if supported by the router) can be effective.
Other protocols, particularly UDP-based services such as SNMP and DNS, could also be leveraged generating alerts using spoofed source IPs, which maybe worth investigating.

 Eito Tamura - Principal Consultant
Eito Tamura - Principal Consultant